Each time a patient visits a clinic or government provider, there is a record created of their personal details- name, contact information, and often their medical history. That information is more than a list in a system, it is private, sensitive information that is at risk if not handled correctly.
The average healthcare data breach costs over $10 million, and organizations can no longer afford the luxury of treating compliance as an afterthought.
HIPAA and SOC 2 are two important data security compliance standards that help protect information and create trust.
In this blog, we summarize why SOC 2 HIPAA compliance matters, best practices for managing a secure queue, and how to identify a data respective digital queuing solution.
Why Data Security Compliance Standards Matter in Queue Systems
Data security compliance standards are formal regulations and guidelines that help organizations manage and protect personal information responsibly. Standards such as HIPAA for healthcare and SOC 2 for broader IT systems are designed to prevent unauthorized access, data leaks, and misuse of sensitive information.
In digital queue systems, compliance is important with regard to data because these platforms often collect and store personal data. A typical system might gather a visitor’s full name, contact details, service history, and, in the case of clinics or public agencies, health-related information. Without strong security protocols, this information can easily be exposed or misused.
Failing to meet these data compliance standards can result in serious consequences, such as:
Legal consequences like fines or lawsuits under HIPAA or GDPR regulations
Reputational damage that erodes public trust and reduces service adoption
Service disruptions caused by breach investigations, shutdowns, or remediation work
Meeting compliance standards is not just a checkbox—it’s an essential part of secure and responsible queue management.
Understanding SOC 2 and HIPAA: The Foundations of Data Compliance
To manage personal information responsibly, queue systems must align with industry-recognized data compliance standards. Two of the most important are SOC 2 and HIPAA. This section breaks down what they are and why they matter for digital queue management.
What is SOC 2 Compliance and Why It Applies to Queue Management
SOC 2 (Service Organization Control 2) is a data compliance framework created by the American Institute of CPAs (AICPA) for service organizations that store customers’ data in the cloud. The compliance framework checks the controls for how the service organization manages data based on five trust service principles:
Security – Protection against unauthorized access
Availability – System operational and available as promised
Processing Integrity – System processes data completely, accurately, and reliably
Confidentiality – Sensitive information is protected from disclosure
Privacy – Personal information is collected, used, retained, disclosed, and disposed of according to the organization's privacy policy
Queue management systems process visitor names, contact information, appointment information, and potentially medical data. Commonly used in a SaaS model by public agencies and healthcare providers, achieving SOC 2 ensures that they are managing sensitive end-user customer data at the highest standard of protection.
For public-sector agencies, choosing a SOC 2-compliant queue system isn't just good practice, it’s a necessary step to ensure service reliability, secure citizen trust, and mitigate data breach risks.
Learn more - Integration & Security
Overview of HIPAA and Its Impact on Queue Management
HIPAA, or the Health Insurance Portability and Accountability Act, is a U.S. law that protects sensitive patient health information from being disclosed without consent or knowledge. In the context of digital queue management, especially in healthcare settings, HIPAA plays a critical role in ensuring that systems handling patient data do so securely and responsibly.
For example, when a patient checks in for an appointment, the digital queue management system could collect Protected Health Information (PHI), including the patient's name, date of birth, the reason for the visit, or their contact number. If PHI is not maintained in a secure and appropriate manner, it can be subject to disclosure, breaches, or unauthorized access, violating that patient's HIPAA rights.
HIPAA enforces three major rules that affect how queue management platforms operate:
Privacy Rule, establishes who can see and disclose PHI
Security Rule, imposes responsibility to have technical, physical, and administrative safeguards over electronic PHI
Breach Notification Rule, requires entities to notify the affected parties and authorities if there has been a breach.
Any digital queue system used in a healthcare environment must be designed with these rules in mind to maintain full HIPAA compliance and protect patient trust.
SOC 2 HIPAA Compliance: Where They Overlap
SOC 2 and HIPAA are separate frameworks, but they often intersect when it comes to protecting sensitive data in digital environments. While SOC 2 is a voluntary compliance standard for service organizations that focuses on five trust service principles—security, availability, processing integrity, confidentiality, and privacy, HIPAA is a federal law specifically designed to protect health information.
Organizations that manage both healthcare and enterprise clients often need to meet SOC2 HIPAA compliance requirements simultaneously. This overlap ensures broader coverage for both industry-specific and general data protection needs.
Here’s where they align:
Access Control - Both SOC2 and HIPAA require user authentication and access through roles.
Encryption - Data has to be encrypted in-transit and at-rest to help prevent disclosure of unauthorized users.
Audit trails - Systems must provide granular audit trails for data access and changes, supporting accountability and breach detection.
Risk Assessments - Regular security risk assessments are mandatory for security implantations and to recognize and mitigate exposures.
For digital queue systems that serve clinics, hospitals, and large businesses, aligning with both standards isn’t just ideal—it’s essential for trust, scalability, and long-term success.
Best Practices for Meeting Data Compliance Standards in Queue Systems
These practices ensure that personal and sensitive information is handled with care, minimizing the risk of breaches or violations.
1. Data Minimization and Purpose Limitation
A fundamental concept of both HIPAA and SOC 2 compliance is that you should gather only the information you absolutely need, and only use collected information to fulfill the intended purpose. In the context of queue management, this means collecting the least amount of information you can manage to notify the citizen, assign the service, and manage wait times.
For example, a government office may need a citizen's name and phone number to notify them of their turn in line, and the clinic may need a patient name and type of service, and there is little to be gained from being asked for five to eight years of their complete health history as they check-in.
Here are best practices that meet the intent of that purpose:
Limit the amount of input fields: For check-in forms, shorter is generally better.
Conditional fields: Ask for additional details only when absolutely required for specific services.
Do not over-collect: If you do not need the information, don't request it or store it. So many unnecessarily details are collected “just in case” it’s needed later.
Automate deletion of information: Set time-based rules for securely deleting or anonymizing data no longer needed.
Review audits regularly: Do a regular review of your systems to ensure unnecessary information is not being captured.
Example:
A public health clinic sets its digital patient check-in system to automatically purge patient contact data 72 hours after the visit unless follow-up is required. This reduces data exposure and ensures compliance with HIPAA’s data retention expectations.
2. End-to-End Data Encryption
End-to-end encryption is an important protective measure in fulfilling data compliance requirements such as SOC 2 and HIPAA. It guarantees that the sensitive data collected by queue management systems is secure at all times, either while it is being transmitted, or when it is stored.
Encryption in transit means that data is securely encoded as it travels between the user’s device and the queue system’s servers. This prevents hackers or unauthorized parties from intercepting information like names, phone numbers, or health details during check-in or notifications.
Encryption at rest refers to encrypting data stored on servers or databases. Even if an unauthorized person gains access to the storage system, the data is still protected, as it is unreadable without the proper decryption keys.
By implementing both types of encryption, organizations can significantly reduce the risk of data breaches and unauthorized access.
Best practices include:
Using TLS (Transport Layer Security) protocols for all data transmissions
Encrypting stored data with strong algorithms like AES-256
Managing encryption keys securely with strict access controls
Regularly updating encryption methods to address new vulnerabilities
Monitoring systems for any signs of unauthorized access or breaches
Example:
A healthcare provider’s digital queue system uses TLS encryption to protect patient data as it’s entered on a kiosk and AES-256 encryption for all stored electronic health records, ensuring compliance with HIPAA’s security rule.
3. Access Controls and Role-Based Permissions
Access controls and role-based permissions are essential for protecting sensitive data in digital queue systems. They ensure that only authorized personnel can view or manage personal information, reducing the risk of accidental exposure or insider threats.
With role-based permissions, organizations assign different access levels based on job functions. For example, frontline staff may only have permission to view basic visitor information needed to assist customers, while administrators have full access to sensitive data and system settings.

Limiting access to sensitive data to administrators mitigates the risk of unauthorized handling of personal or health information. It also makes it easier to track who accessed what data and when, supporting compliance requirements for audit trails.
Key practices include:
Defining clear roles and access levels for all employees
Enforcing strong authentication methods (e.g., multi-factor authentication)
Regularly reviewing and updating access permissions
Logging access attempts and changes for accountability
Restricting administrative rights to a small, trusted group
Example:
A government office using a queue system allows clerks to see only names and appointment times, while IT administrators control encryption keys and full database access, ensuring sensitive data remains protected.
4. Audit Logs and Activity Monitoring
Audit logs and activity monitoring play a crucial role in maintaining data security and compliance in queue management systems. These tools record detailed information about who accessed the system, what data they viewed or modified, and when these actions took place.
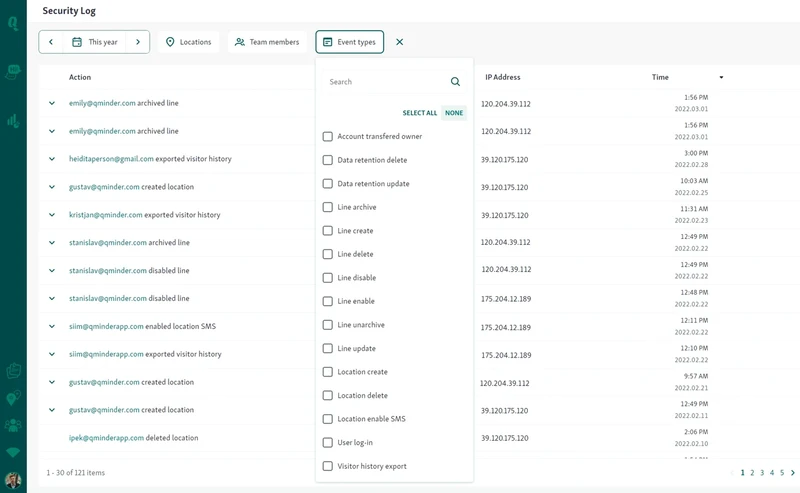
Keeping accurate audit logs helps organizations quickly identify unauthorized access or suspicious behavior, enabling faster incident response. They also provide a transparent record that demonstrates compliance with regulations like SOC 2 and HIPAA, which require accountability for data handling.
Best practices include:
Automatically logging all user activity within the queue system
Monitoring logs regularly to spot unusual patterns or breaches
Protecting log data from tampering or deletion
Using logs to investigate and resolve security incidents
Retaining logs for the duration required by compliance standards
Example:
A healthcare clinic’s queue system logs every staff login, patient record access, and data update. If a breach is suspected, administrators review these logs to trace unauthorized actions and take corrective measures immediately.
5. Regular Compliance Audits and Risk Assessments
Maintaining data compliance standards requires ongoing vigilance through regular audits and risk assessments. Third-party auditors provide an independent review of the security practices of your queue system and identify which areas are non-compliant with standards such as SOC 2 and HIPAA.
These types of external audits provide insight, validation, and evidence that your data protection compliance practices meet required industry standards. In addition to third-party audits, conducting internal audits every 6 to 12 months ensures your organization is staying ahead of the game.
Key actions include:
Engaging qualified auditors for comprehensive compliance evaluations
Conducting internal audits regularly to catch issues early
Updating policies and security controls based on audit findings
Documenting audit results and remediation efforts
Training staff on compliance requirements and best practices
Example:
A healthcare provider using a digital queue system scheduled annual third-party SOC 2 audits and quarterly internal risk assessments. This approach helped them identify and fix vulnerabilities before any breach occurred, ensuring continuous HIPAA compliance and safeguarding patient data.
Read more - Data security in Qminder
Choosing a Queue Management System With Built-In SOC2 HIPAA Compliance
Selecting the right queue management system isn’t just about convenience and efficiency—it’s also about ensuring that every touchpoint is secure and compliant with data security regulations.
For organizations in healthcare, government, and other service-driven industries, it's crucial to choose software that has built-in SOC 2 and HIPAA compliance features.
Key Features to Look For:
Encrypted Communications
Ensure the system uses end-to-end encryption (both in transit and at rest) to protect sensitive data like names, contact details, and medical information.
Consent Forms
System-generated consent forms that describe how personal data will be used and stored, will help provide general data protection and HIPAA protections.
Data Retention Policies
The software should be flexible in allowing you to determine how long data will be stored (in terms of user data and generated/collected health data) and provide automated deletion mechanisms that comply with your obligations.
Secure Cloud Infrastructure
Look for platforms that operate on SOC 2-certified cloud providers and offer multi-tenant security with logical data separation.
Questions to Ask Vendors:
Are you SOC 2 Type II certified?
This signifies the vendor’s systems and operations were audited independently over time for compliance with the five trust principles.
Do you sign Business Associate Agreements (BAAs)?
A BAA is required under HIPAA when a vendor processes Protected Health Information (PHI) on your behalf.
How do you handle data deletion?
Ask if the system has automatic data deletion methods after a set time and how manual data deletion requests will be handled to deliberate compliance.
Secure Queues Start With Smart Compliance
HIPAA and SOC 2 compliance aren’t just checkboxes—they’re the foundation of secure, trustworthy queue management in today’s data-driven world. Whether you're managing patient intake at a clinic or handling visitor check-ins at a public agency, protecting personal information must be a top priority.
By following data security compliance standards like encryption, access control, and regular audits, organizations can avoid costly breaches, build public trust, and improve service delivery.
Qminder is built with both operational efficiency and compliance in mind, supporting HIPAA and SOC 2 requirements out of the box.
Ready to simplify compliance and secure your queue system? Try Qminder today.
The key difference is that SOC 2 Type I examines the design of a company’s security controls at a specific moment in time, while SOC 2 Type II assesses how effective those controls are over a defined period of time (typically 3 to 12 months). Therefore, a Type II provides much stronger assurance of ongoing data protection practices.
Yes. Most modern queue systems are affordable and have HIPAA-compliant and SOC 2-compliant features. In fact, companies such as Qminder have scalable queue management solutions that possess the security features of large expensive enterprise systems.
HIPAA rules are often stable, but they may be occasionally updated, mostly by following technology changes or serious breaches. SOC 2 rules are often updated by the AICPA due to new cybersecurity threats.